Software Engineering Multiple Choice Questions & Answers (MCQs) “Software Engineering Ethics – 1”.
a) Confidentiality
b) Intellectual property rights
c) Both Confidentiality & Intellectual property rights
d) Managing Client Relationships
Explanation: Engineers should normally respect the confidentiality of their employers or clients irrespective of whether or not a formal confidentiality agreement has been signed.
They should be aware of local laws governing the use of intellectual property such as patents, copyright, etc.
2. “Software engineers should not use their technical skills to misuse other people’s computers.”Here the term misuse refers to:
a) Unauthorized access to computer material
b) Unauthorized modification of computer material
c) Dissemination of viruses or other malware
d) All of the mentioned
Explanation: None.
3. Explain what is meant by PRODUCT with reference to one of the eight principles as per the ACM/IEEE Code of Ethics ?
a) The product should be easy to use
b) Software engineers shall ensure that their products and related
modifications meet the highest professional standards possible
c) Software engineers shall ensure that their products and related modifications satisfy the client
d) It means that the product designed /created should be easily available
Explanation: None.
4. Identify an ethical dilemma from the situations mentioned below:
a) Your employer releases a safety-critical system without finishing the testing of the system
b) Refusing to undertake a project
c) Agreement in principle with the policies of senior management
d) All of the mentioned
Explanation: None.
5. Identify the correct statement: “Software engineers shall
a) act in a manner that is in the best interests of his expertise and favour.”
b) act consistently with the public interest.”
c) ensure that their products only meet the SRS.”
d) all of the mentioned
Explanation: Software engineers shall act in a manner that is in the best interests of their client and employer consistent with the public interest and shall ensure that their products and related modifications meet the highest professional standards possible.Thus options a & c are ruled out.
6. Select the incorrect statement: “Software engineers should
a) not knowingly accept work that is outside your competence.”
b) not use your technical skills to misuse other people’s computers.”
c) be dependent on their colleagues.”
d) maintain integrity and independence in their professional judgment.”
Explanation:None.
7. Efficiency in a software product does not include ________
a) responsiveness
b) licensing
c) memory utilization
d) processing time
Explanation: Licensing of a software product comes under corporate part of the software company.
8. As per an IBM report, “31%of the project get cancelled before they
are completed, 53% overrun their cost estimates by an average of 189%
and for every 100 projects, there are 94 restarts”.What is the reason
for these statistics ?
a) Lack of adequate training in software engineering
b) Lack of software ethics and understanding
c) Management issues in the company
d) All of the mentioned
Explanation: Option b & c are a part of Software Engineering as a subject,hence option a covers them both.
9. The reason for software bugs and failures is due to
a) Software companies
b) Software Developers
c) Both Software companies and Developers
d) All of the mentioned
Explanation: Software companies are responsible for making policies and providing working atmosphere for the software development, so in turn these companies become a part of software development process.Bugs from developers side is no new thing. Thus option c answers the question.
10. Company has latest computers and state-of the- art software tools, so we shouldn’t worry about the quality of the product.
a) True
b) False
Explanation: The infrastructure is only one of the several factors that determine the quality of the product.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Life Cycle Models”.
1. Build & Fix Model is suitable for programming exercises of ___________ LOC (Line of Code).
a) 100-200
b) 200-400
c) 400-1000
d) above 1000
Explanation: Build & Fix Model is suitable for small projects & programming exercises of 100 or 200 lines.
2. RAD stands for
a) Relative Application Development
b) Rapid Application Development
c) Rapid Application Document
d) None of the mentioned
Explanation: None.
3. Which one of the following models is not suitable for accommodating any change?
a) Build & Fix Model
b) Prototyping Model
c) RAD Model
d) Waterfall Model
Explanation: Real projects rarely follow the sequential flow that the Waterfall Model proposes.
4. Which is not one of the types of prototype of Prototyping Model?
a) Horizontal Prototype
b) Vertical Prototype
c) Diagonal Prototype
d) Domain Prototype
Explanation: Their is no such thing as Diagonal Prototype whereas other options have their respective definitions.
5. Which one of the following is not a phase of Prototyping Model?
a) Quick Design
b) Coding
c) Prototype Refinement
d) Engineer Product
Explanation: A prototyping model generates only a working model of a system.
6. Which of the following statements regarding Build & Fix Model is wrong?
a) No room for structured design
b) Code soon becomes unfixable & unchangeable
c) Maintenance is practically not possible
d) It scales up well to large projects
Explanation: Build & Fix Model is suitable for 100-200 LOC
7. RAD Model has
a) 2 phases
b) 3 phase
c) 5 phases
d) 6 phases
Explanation: RAD Model consists of five phases namely:Business modeling,Data modeling,Process modeling,Application generation and Testing & Turnover.
8. What is the major drawback of using RAD Model?
a) Highly specialized & skilled developers/designers are required
b) Increases reusability of components
c) Encourages customer/client feedback
d) Increases reusability of components, Highly specialized & skilled developers/designers are required
Explanation: The client may create an unrealistic product vision leading a team to over or under-develop functionality.Also, the specialized & skilled developers are not easily available.
9. SDLC stands for
a) Software Development Life Cycle
b) System Development Life cycle
c) Software Design Life Cycle
d) System Design Life Cycle
Explanation: None.
10. Which model can be selected if user is involved in all the phases of SDLC?
a) Waterfall Model
b) Prototyping Model
c) RAD Model
d) both Prototyping Model & RAD Model
Explanation: None.
This set of Software Engineering Questions and Answers for Campus interviews focuses on “Evolutionary Software Process Models”.
1. Which one of the following is not an Evolutionary Process Model?
a) WINWIN Spiral Model
b) Incremental Model
c) Concurrent Development Model
d) All of the mentioned
Explanation: None.
2. The Incremental Model is a result of combination of elements of which two models?
a) Build & FIX Model & Waterfall Model
b) Linear Model & RAD Model
c) Linear Model & Prototyping Model
d) Waterfall Model & RAD Model
Explanation: Each linear sequence produces a deliverable “increment” of the software and particularly when we have to quickly deliver a limited functionality system.
3. What is the major advantage of using Incremental Model?
a) Customer can respond to each increment
b) Easier to test and debug
c) It is used when there is a need to get a product to the market early
d) Easier to test and debug & It is used when there is a need to get a product to the market early
Explanation: Incremental Model is generally easier to test and debug than other methods of software development because relatively smaller changes are made during each iteration and is popular particularly when we have to quickly deliver a limited functionality system.However, option “a” can be seen in other models as well like RAD model,hence option “d” answers the question.
4. The spiral model was originally proposed by
a) IBM
b) Barry Boehm
c) Pressman
d) Royce
Explanation: None.
5. The spiral model has two dimensions namely _____________ and ____________
a) diagonal, angular
b) radial, perpendicular
c) radial, angular
d) diagonal, perpendicular
Explanation: The radial dimension of the model represents the cumulative costs and the angular dimension represents the progress made in completing each cycle. Each loop of the spiral from X-axis clockwise through 360o represents one phase.
6. How is WINWIN Spiral Model different from Spiral Model?
a) It defines tasks required to define resources, timelines, and other project related information
b) It defines a set of negotiation activities at the beginning of each pass around the spiral
c) It defines tasks required to assess both technical and management risks
d) It defines tasks required to construct, test, install, and provide user support
Explanation: Except option “b” all other tasks/activities are present in Spiral Model as well.
7. Identify the disadvantage of Spiral Model.
a) Doesn’t work well for smaller projects
b) High amount of risk analysis
c) Strong approval and documentation control
d) Additional Functionality can be added at a later date
Explanation: All other options are the advantages of Spiral Model.
8. Spiral Model has user involvement in all its phases.
a) True
b) False
Explanation: None.
9. How is Incremental Model different from Spiral Model?
a) Progress can be measured for Incremental Model
b) Changing requirements can be accommodated in Incremental Model
c) Users can see the system early in Incremental Model
d) All of the mentioned
Explanation: None.
10. If you were to create client/server applications, which model would you go for?
a) WINWIN Spiral Model
b) Spiral Model
c) Concurrent Model
d) Incremental Model
Explanation: When applied to client/server applications, the concurrent process model defines activities in two dimensions: a system dimension and a component dimension.Thus Concurrency is achieved by system and component activities occurring simultaneously and can be modeled using the state-oriented approach.
This set of Software Engineering Questions and Answers for Freshers focuses on “Software Process and Product – 2”.
1. If a software production gets behind schedule, one can add more programmers and catch up.
a) True
b) False
Explanation: As new people are added, people who were working must spend time educating the newcomers, thereby reducing the amount of time spent on productive development effort.
2. Choose an internal software quality from given below:
a) scalability
b) usability
c) reusability
d) reliability
Explanation: rest all are external qualities which are visible to the user.
3. RUP stands for____________ created by a division of ____________
a) Rational Unified Program, IBM
b) Rational Unified Process, Infosys
c) Rational Unified Process, Microsoft
d) Rational Unified Process, IBM
Explanation: None.
4. The RUP is normally described from three perspectives-dynamic, static & practice.What does static perspective do ?
a) It shows the process activities that are enacted
b) It suggests good practices to be used during the process
c) It shows the phases of the model over time
d) All of the mentioned
Explanation: None.
5. The only deliverable work product for a successful project is the working program.
a) True
b) False
Explanation: A working program is only one part of a software configuration that includes many elements. Documentation provides a foundation for successful engineering and, more important, guidance for software support.
6. Which phase of the RUP is used to establish a business case for the system ?
a) Transition
b) Elaboration
c) Construction
d) Inception
Explanation: None.
7. Which one of the following is not a fundamental activity for software processes in software engineering ?
a) Software Verification
b) Software Validation
c) Software design and implementation
d) Software evolution
Explanation: Software Verification is accounted for in implementation & testing activity.
8. A general statement of objectives is the major cause of failed software efforts.
a) True
b) False
Explanation: A formal and detailed description of the information domain, function, behavior, performance, interfaces, design constraints and validation criteria is essential which can be determined only after thorough communication between customer and developer.
9. The longer a fault exists in software
a) the more tedious its removal becomes
b) the more costly it is to detect and correct
c) the less likely it is to be properly corrected
d) All of the mentioned
Explanation: None.
10. Component-based Software Engineering allows faster delivery.
a) True
b) False
Explanation: Due to using previously tested components they produce more reliable system at a faster rate.
11. Arrange the following steps to form a basic/general Engineering Process Model.
i. Test
ii. Design
iii. Install
iv. Specification
v. Manufacture
vi. Maintain
a) 2, 4, 5, 1, 6, 3
b) 4, 2, 5, 1, 3, 6
c) 2, 4, 5, 1, 3, 6
d) 4, 2, 5, 1, 6, 3
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Requirement Engineering”.
1. What are the types of requirements ?
a) Availability
b) Reliability
c) Usability
d) All of the mentioned
Explanation: All the mentioned traits are beneficial for an effective product to be developed.
2. Select the developer-specific requirement ?
a) Portability
b) Maintainability
c) Availability
d) Both Portability and Maintainability
Explanation: Availability is user specific requirement.
3. Which one of the following is not a step of requirement engineering?
a) elicitation
b) design
c) analysis
d) documentation
Explanation: Requirement Elicitation, Requirement Analysis, Requirement Documentation and Requirement Review are the four crucial process steps of requirement engineering.Design is in itself a different phase of Software Engineering.
4. FAST stands for
a) Functional Application Specification Technique
b) Fast Application Specification Technique
c) Facilitated Application Specification Technique
d) None of the mentioned
Explanation: None.
5. QFD stands for
a) quality function design
b) quality function development
c) quality function deployment
d) none of the mentioned
Explanation: None.
6. A Use-case actor is always a person having a role that different people may play.
a) True
b) False
Explanation: Use-case Actor is anything that needs to interact with the system, be it a person or another (external) system.
7. The user system requirements are the parts of which document ?
a) SDD
b) SRS
c) DDD
d) SRD
Explanation: Software requirements specification (SRS), is a complete description of the behaviour of a system to be developed and may include a set of use cases that describe interactions the users will have with the software.
8. A stakeholder is anyone who will purchase the completed software system under development.
a) True
b) False
Explanation: Stakeholders are anyone who has an interest in the project. Project stakeholders are individuals and organizations that are actively involved in the project, or whose interests may be affected as a result of project execution or project completion.
9. Conflicting requirements are common in Requirement Engineering,
with each client proposing his or her version is the right one.
a) True
b) False
Explanation: This situation is seen in every field of work as each professional has his/her way of looking onto things & would argue to get his/her point approved.
10. Which is one of the most important stakeholder from the following ?
a) Entry level personnel
b) Middle level stakeholder
c) Managers
d) Users of the software
Explanation: Users are always the most important stakeholders.After all, without users or customers, what’s the point of being in business?.
This set of Software Engineering Interview Questions and Answers for freshers focuses on “Requirement Elicitation Techniques – 2”.
1. How is brainstorming different from JAD ? Brainstorming sessions
a) last for about 2-3 hours
b) last for about 2-3 days
c) cover the technology used for the development
d) all of the mentioned
Explanation: Brainstorming is a group or individual creativity technique by which efforts are made to find a conclusion for a specific problem by gathering a list of ideas spontaneously contributed by its member(s).The idea is to quickly reach to an approved solution ASAP.
2. How is throwaway prototype different from evolutionary prototype ?
a) It involves successive steps
b) It involves just one task
c) The prototype is built with the idea that it will eventually be converted into final system
d) It has a shorter development time
Explanation: Except option b all other options represent the characteristics of an evolutionary prototype.
3. Keeping the requirements of QFD in mind which of the following is not an example of an Expected Requirement ?
a) Ease of software installation
b) Overall operational correctness and reliability
c) Specific system functions
d) Quality graphical display
Explanation: Expected requirements are so fundamental that a customer does not explicitly state them.System functions comes under the category of Normal requirements in QFD which is compulsory to be defined,hence is not an expected requirement.
4. QFD works best if it has management commitment.
a) True
b) False
Explanation: QFD involves heavy investment in initial stages, thus bounding the management to provide appropriate funding for the development process .
5. Which of the following Requirement Elicitation Techniques is
applicable to messy, changing and ill-defined problem situations ?
a) Quality Function Deployment (QFD)
b) Prototyping
c) Soft Systems Methodology (SSM)
d) Controlled Requirements Expression (CORE)
Explanation: Soft systems methodology (SSM) is a systemic approach for tackling real-world problematic situations.It is a common misunderstanding that SSM is a methodology for dealing solely with ‘soft problems’ (problems which involve psychological, social, and cultural elements). SSM does not differentiate between ‘soft’ and ‘hard’ problems, it merely provides a different way of dealing with situations perceived as problematic.
6. To ensure that a given root definition is rigorous and
comprehensive, The Lancaster team proposed several criteria that are
summarized in the mnemonic CATWOE in Soft Systems Methodology
(SSM).Which of the following alphabet is representing an entirely
different meaning to SSM ?
a) C – Customer
b) A – Actor
c) T – Transformation
d) E – ER Model
Explanation: ‘E’ in CATWOE stands for Environmental constraints.
7. Choose the disadvantage of using SSM as an elicitation technique.
a) It incorporates human element into design
b) SSM is in its infant stage
c) SSM is suitable for new systems
d) Standard methodologies like Role Exploration, Issue Resolution and Reorganization support SSM
Explanation: SSM is still in its infancy.It is evolving and its industrial usage is low.
8. How many phases are there in Brainstorming ?
a) Two
b) Three
c) Four
d) All of the mentioned
Explanation: Preparation, Execution and Follow up are the three phases to be achieved for a successful brainstorming session.
9. Who controls the FAST (Facilitated Application Specification Techniques) meeting ?
a) System Analyst
b) Scribe
c) Facilitator
d) Manager
Explanation: A Facilitator (a customer/developer/an outsider) controls the FAST meeting.His role is to ensure that the meeting is productive.
10. Arrange the steps in order to represent the conducting of Wideband Delphi Technique.
i. Conduct a group discussion
ii. Conduct another group discussion
iii. Present experts with a problem
iv. Collect expert opinion anonymously
v. Iterate until consensus is reached
vi. Feedback a summary of result to each expert
a) i, iii, ii, iv, v, vi
b) iii, i, ii, iv, v, vi
c) i, ii, iii, iv, vi, v
d) iii, i, iv, vi, ii, v
Explanation: The sequence represents the working steps of a Wideband Delphi technique .
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “System Modelling – 1”.
1. The Unified Modeling Language (UML) has become an effective
standard for software modelling.How many different notations does it
have ?
a) Three
b) Four
c) Six
d) Nine
Explanation: The different notations of UML includes the nine UML diagrams namely class, object, sequence, collaboration, activity, state-chart, component, deployment and use case diagrams.
2. Which model in system modelling depicts the dynamic behaviour of the system ?
a) Context Model
b) Behavioral Model
c) Data Model
d) Object Model
Explanation: Behavioral models are used to describe the dynamic behavior of an executing system. This can be modeled from the perspective of the data processed by the system or by the events that stimulate responses from a system.
3. Which model in system modelling depicts the static nature of the system ?
a) Behavioral Model
b) Context Model
c) Data Model
d) Structural Model
Explanation: Structural models show the organization and architecture of a system. These are used to define the static structure of classes in a system and their associations.
4. Which perspective in system modelling shows the system or data architecture.
a) Structural perspective
b) Behavioral perspective
c) External perspective
d) All of the mentioned
Explanation: Structural perspective is used to define the static structure of classes in a system and their associations.
5. Which system model is being depicted by the ATM operations shown below:
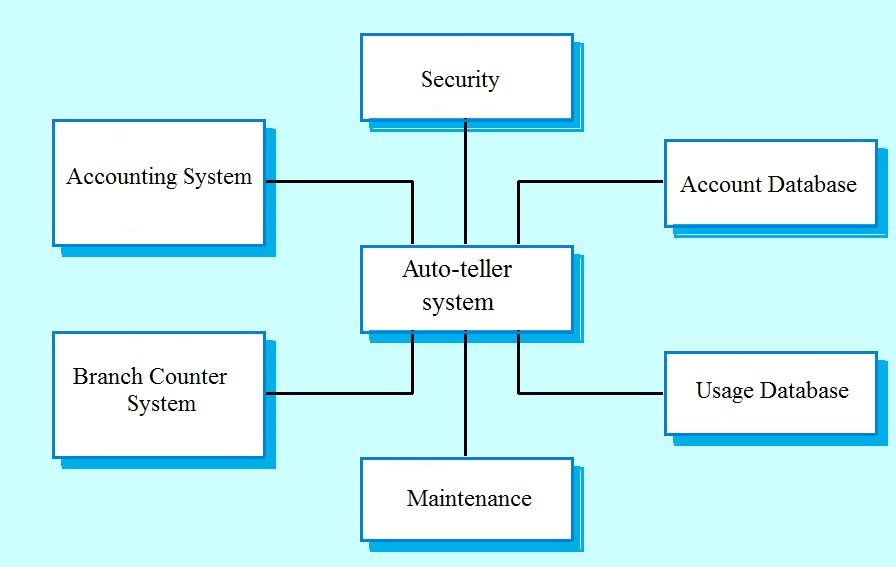
a) Structural model
b) Context model
c) Behavioral model
d) Interaction model
Explanation: Context models are used to illustrate the operational context of a system.They show what lies outside the system boundaries.
6. Activity diagrams are used to model the processing of data.
a) True
b) False
Explanation: The statement mentioned is true and each activity represents one process step.
7. Model-driven engineering is just a theoretical concept. It cannot be converted into a working/executable code.
a) True
b) False
Explanation: Model-driven engineering is an approach to software development in which a system is represented as a set of models that can be automatically transformed to executable code.
8. The UML supports event-based modeling using ____________ diagrams.
a) Deployment
b) Collaboration
c) State chart
d) All of the mentioned
Explanation: State diagrams show system states and events that cause transitions from one state to another.
This set of Software Engineering Questions and Answers for Experienced people focuses on “System Modelling – 2”.
1. Which of the following diagram is not supported by UML considering Data-driven modeling ?
a) Activity
b) Data Flow Diagram (DFD)
c) State Chart
d) Component
Explanation: DFDs focus on system functions and do not recognize system objects.
2. _________________ allows us to infer that different members of classes have some common characteristics.
a) Realization
b) Aggregation
c) Generalization
d) dependency
Explanation: Generalization is an everyday technique that we use to manage complexity.This means that common information will be maintained in one place only.
3. One creates Behavioral models of a system when you are discussing and designing the system architecture.
a) True
b) False
Explanation: Structural models of software display the organization of a system in terms of the components that make up that system and their relationships.
4. ______________ & ______________ diagrams of UML represent Interaction modeling.
a) Use Case, Sequence
b) Class, Object
c) Activity, State Chart
d) All of the mentioned
Explanation: Use case modeling is mostly used to model interactions between a system and external actors.Sequence diagrams are used to model interactions between system components, although external agents may also be included.
5. Which level of Entity Relationship Diagram (ERD) models all entities and relationships ?
a) Level 1
b) Level 2
c) Level 3
d) Level 4
Explanation: Level 1 ERD models all data objects (entities) and their “connections” to one another while Level 3 ERD models all entities, relationships, and the attributes that provide further depth. Thus option b is correct.
6. ___________ classes are used to create the interface that the user sees and interacts with as the software is used.
a) Controller
b) Entity
c) Boundary
d) Business
Explanation: The answer is self-explanatory.
7. Which of the following statement is incorrect regarding the Class-responsibility-collaborator (CRC) modeling ?
a) All use-case scenarios (and corresponding use-case diagrams) are organized into categories in CRC modelling
b) The review leader reads the use-case deliberately
c) Only developers in the review (of the CRC model) are given a subset of the CRC model index cards
d) All of the mentioned
Explanation: All participants in the review (of the CRC model) are given a subset of the CRC model index cards.
8. A data object can encapsulates processes and operation as well.
a) True
b) False
Explanation: A data object encapsulates data only. There is no reference within a data object to operations that act on the data.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Evolution”.
1. The two dimensions of spiral model are
a) diagonal, angular
b) radial, perpendicular
c) radial, angular
d) diagonal, perpendicular
Explanation: The radial dimension depicts the cumulative costs and the angular dimension depicts the progress made in completing each cycle. Each loop of the spiral model represents a phase.
2. The Incremental Model is combination of elements of
a) Build & FIX Model & Waterfall Model
b) Linear Model & RAD Model
c) Linear Model & Prototyping Model
d) Waterfall Model & RAD Model
Explanation: Each linear sequence produces a deliverable “increment” of the software system, particularly needed in case of quick delivery of a limited functionality system..
3. Model preferred to create client/server applications is
a) WINWIN Spiral Model
b) Spiral Model
c) Concurrent Model
d) Incremental Model
Explanation: In case of client/server applications, the concurrent process model specifies activities in two dimensions: a system dimension and a component dimension. Hence Concurrency is achieved by these two activities occurring simultaneously and can be modeled using the state-oriented approach.
4. Identify the correct statement with respect to Evolutionary development:
a) Evolutionary development usually has two flavors; exploratory development, and throw-away prototyping
b) Very large projects are usually done using evolutionary development based approach
c) It facilitates easy project management, through the high volume of documentation it generates
d) Sometimes the construction of a throw-away prototype is not followed
by a re- implementation of the software system using a more structured
approach
Explanation: Evolutionary development usually has two flavors; exploratory development, and
throw-away prototyping.
5. Spiral model was developed by
a) Victor Bisili
b) Berry Boehm
c) Bev Littlewood
d) Roger Pressman
Explanation: Berry Boehm in 1986 in his Article “A spiral model of software development and enhancement”.
6. Software evolution does not comprises:
a) Development activities
b) Negotiating with client
c) Maintenance activities
d) Re-engineering activities
Explanation: Software evolution refers to the study and management of the process of making changes to software over time. Thus it comprises rest three options.
7. Processes for evolving a software product depend on:
a) Type of software to be maintained
b) Development processes used
c) Skills and experience of the people involved
d) All of the mentioned
Explanation: Processes used for software evolution depend on all these factors.
8. Which technique is applied to ensure the continued evolution of legacy systems ?
a) Forward engineering
b) Reverse Engineering
c) Reengineering
d) Reverse Engineering and Reengineering
Explanation: Processes used for software evolution depend rely on these two techniques.
9. Program modularization and Source code translation are the activities of_____________
a) Forward engineering
b) Reverse Engineering
c) Reengineering
d) Reverse Engineering and Reengineering
Explanation: Reengineering is the examination and alteration of a subject system to reconstitute it in a new form and the subsequent implementation of the new form.
10. Reverse engineering is the last activity in a reengineering project.
a) True
b) False
Explanation: Reverse engineering is often the initial activity in a reengineering project.
11. The cost of re-engineering is often significantly less than the costs of developing new software.
a) True
b) False
Explanation: There is a high risk in new software development. There may be development problems, staffing problems and specification problems, thereby increasing the cost.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Sociotechnical Systems”.
1. A sociotechnical system is a system that includes
a) people
b) software
c) hardware
d) all of the mentioned
Explanation: A sociotechnical system is a system that includes people, software, and hardware to show that you need to take a systems perspective on security and dependability.
2. Which layer is missing in the sociotechnical system stack as shown below:
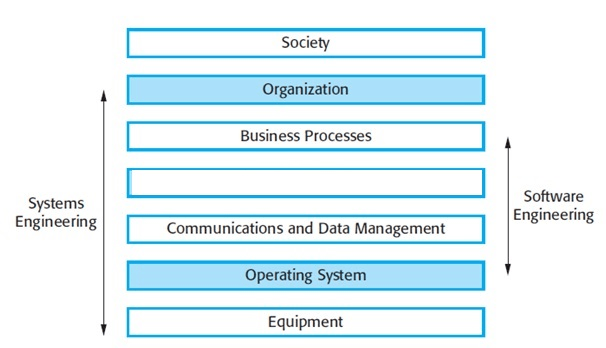
a) organizational layer
b) application layer
c) physical layer
d) transport layer
Explanation: The application layer This layer delivers the application-specific functionality
that is required.
3. Consider an example of a system which has a police command and
control system that may include a geographical information system to
provide details of the location of incidents. What kind of system the
example represents?
a) Complex System
b) Technical computer-based system
c) Sociotechnical System
d) Both Complex and Sociotechnical System
Explanation: Complex systems are usually hierarchical and so include other systems.
4. Which property of a sociotechnical system varies depending on how the component assemblies are arranged and connected?
a) security
b) usability
c) volume
d) reliability
Explanation: The volume of a system (the total space occupied) varies depending on how the component assemblies are arranged and connected.
5. Which property of a sociotechnical system depends on the technical
system components, its operators, and its operating environment?
a) security
b) usability
c) volume
d) reliability
Explanation: Usability reflects how easy it is to use the system.
6. In a sociotechnical system, you need to consider reliability from perspectives namely:
a) only software reliability
b) only hardware reliability
c) hardware and software reliability
d) hardware, software and operator reliability
Explanation: In a sociotechnical system, you need to consider reliability from all three perspectives.
7. There are ________ overlapping stages in the lifetime of large and complex sociotechnical systems.
a) two
b) three
c) four
d) five
Explanation: The stages are Procurement, Development and Operation.
8. Sociotechnical systems are deterministic.
a) True
b) False
Explanation: Sociotechnical systems are non-deterministic partly because they include people and partly because changes to the hardware, software, and data in these systems are so frequent
9. What are the two ways to view the human error of a sociotechnical system?
a) hardware and software approach
b) management and users approach
c) person and systems approach
d) all of the mentioned
Explanation: The answer is self explanatory.
10. Human and organizational factors such as organizational structure
and politics have a significant effect on the operation of
sociotechnical systems.
a) True
b) False
Explanation: As people are a part of the system, hence they affect the sociotechnical system.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Dependability and Security”.
1. A characteristic of a software system that can lead to a system error is known as?
a) Human error or mistake
b) System fault
c) System error
d) System failure
Explanation: None.
2. An erroneous system state that can lead to system behavior that is unexpected by system users is known as?
a) Human error or mistake
b) System fault
c) System error
d) System failure
Explanation: None.
3. An event that occurs at some point in time when the system does
not deliver a service as expected by its users is called _____________
a) Human error or mistake
b) System fault
c) System error
d) System failure
Explanation: None.
4. A chemical plant system may detect excessive pressure and open a
relief valve to reduce these pressures before an explosion occurs. What
kind of dependability and security issue the example states?
a) Hazard avoidance
b) Damage limitation
c) Hazard detection
d) Hazard detection and removal
Explanation: The system is designed so that hazards are detected and removed before they result in an accident.
5. An aircraft engine normally includes automatic fire
extinguishers.What kind of dependability and security issue the example
states?
a) Hazard avoidance
b) Damage limitation
c) Hazard detection
d) Hazard detection and removal
Explanation: The system may include protection features that minimize the damage that may result from an accident.
6. An assessment of the worst possible damage that could result from a particular hazard is known as
a) Risk
b) Hazard probability
c) Hazard severity
d) Mishap
Explanation: Hazard severity can range from catastrophic, where many people are killed, to minor, where only minor damage results. When an individual death is a possibility, a reasonable assessment of hazard severity is ‘very high’.
7. which of the following terms is a measure of the probability that the system will cause an accident?
a) Risk
b) Hazard probability
c) Accident
d) Damage
Explanation: The risk is assessed by considering the hazard probability, the hazard severity, and the probability that the hazard will lead to an accident.
8. A weakness in a computer-based system that may be exploited to cause loss or harm is known as?
a) Vulnerability
b) Attack
c) Threat
d) Exposure
Explanation: None.
9. A password checking system that disallows user passwords that are
proper names or words that are normally included in a dictionary is an
example of ___________ with respect to security systems.
a) risk
b) control
c) attack
b) asset
Explanation: A control protective measure that reduces a system’s vulnerability.
10. The safety of a system is a system attribute that reflects the
system’s ability to operate, normally or abnormally, without injury to
people or damage to the environment.
a) True
b) False
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Security Engineering”.
1. Which of the following is a layer of protection for Security ?
a) Platform-level protection
b) Application-level protection
c) Record-level protection
d) All of the mentioned
Explanation: None.
2. Security engineering is only concerned with maintenance of systems such that they can resist malicious attacks.
a) True
b) False
Explanation: Security engineering is concerned with maintenance as well as development of such systems.
3. What are security controls ?
a) Controls that are intended to ensure that attacks are unsuccessful
b) Controls that are intended to detect and repel attacks
c) Controls that are intended to support recovery from problems
d) All of the mentioned
Explanation: All the options define a security control property.
4. Controls that are intended to repel attacks is analogous to ____________ in dependability engineering.
a) Fault avoidance
b) Fault tolerance
c) Fault detection
d) None of the mentioned
Explanation: Here the system is designed so that faults in the delivered software do not result in system failure.
5. Controls that are intended to ensure that attacks are unsuccessful is analogous to ____________ in dependability engineering.
a) Fault avoidance
b) Fault tolerance
c) Fault detection
d) Fault Recovery
Explanation: In Fault avoidance the system is developed in such a way that human error is avoided and thus system faults are minimised.
6. What is Life cycle risk assessment ?
a) Risk assessment before the system has been deployed
b) Risk assessment while the system is being developed
c) All of the mentioned
d) None of the mentioned
Explanation: None.
7. A system resource that has a value and has to be protected is known as
a) Asset
b) Control
c) Vulnerability
d) None of the mentioned
Explanation: The answer is self explanatory.
8. An impersonation of an authorised user is an example of a security threat.
a) True
b) False
Explanation: It is a security attack.
9. The records of each patient that is receiving or has received treatment resembles which security concept ?
a) Asset
b) Threat
c) Vulnerability
d) Control
Explanation: Asset is a system resource that has a value and has to be protected.
10. Circumstances that have potential to cause loss or harm is known as
a) Attack
b) Threat
c) Vulnerability
d) Control
Explanation: The answer is self explanatory.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Design”.
1. Which is the first step in the software development life cycle ?
a) Analysis
b) Design
c) Problem/Opportunity Identification
d) Development and Documentation
Explanation: None.
2. Which tool is use for structured designing ?
a) Program flowchart
b) Structure chart
c) Data-flow diagram
d) Module
Explanation: A Structure Chart (SC) in software engineering and organizational theory, is a chart which shows the breakdown of a system to its lowest manageable levels.
3. A step by step instruction used to solve a problem is known as
a) Sequential structure
b) A List
c) A plan
d) An Algorithm
Explanation: None.
4. In the Analysis phase, the development of the ____________ occurs,
which is a clear statement of the goals and objectives of the project.
a) documentation
b) flowchart
c) program specification
d) design
Explanation: Program specification is the definition of what a computer program is expected to do.
5. Actual programming of software code is done during the ____________ step in the SDLC.
a) Maintenance and Evaluation
b) Design
c) Analysis
d) Development and Documentation
Explanation: The developer has to find in the technical documentation enough information to start coding.
6. Who designs and implement database structures.
a) Programmers
b) Project managers
c) Technical writers
d) Database administrators
Explanation: The role of database administrators includes the development and design of database strategies, system monitoring and improving database performance and capacity, and planning for future expansion requirements.
7. ____________ is the process of translating a task into a series of commands that a computer will use to perform that task.
a) Project design
b) Installation
c) Systems analysis
d) Programming
Explanation: None.
8. Debugging is:
a) creating program code
b) finding and correcting errors in the program code
c) identifying the task to be computerized
d) creating the algorithm
Explanation: Debugging is a methodical process of finding and reducing the number of bugs, or defects, in a computer program or a piece of electronic hardware, thus making it behave as expected.
9. In Design phase, which is the primary area of concern ?
a) Architecture
b) Data
c) Interface
d) All of the mentioned
Explanation: Part of the design phase is to create structural and behavioral models of the system which is covered by architecture, data and the interface of the product.
10. The importance of software design can be summarized in a single word which is:
a) Efficiency
b) Accuracy
c) Quality
d) Complexity
Explanation: Software functional quality reflects how well it complies with or conforms to a given design, based on functional requirements or specifications.
11. Cohesion is a qualitative indication of the degree to which a module
a) can be written more compactly
b) focuses on just one thing
c) is able to complete its function in a timely manner
d) is connected to other modules and the outside world
Explanation: Cohesion of a single module/component is the degree to which its responsibilities form a meaningful unit.
Explanation: Coupling between modules/components is their degree of mutual interdependence.
This set of Software Engineering online quiz focuses on “Function Oriented Design using Structured Analysis Structured Design”.
1. SA/SD features are obtained from which of the methodologies?
a) Constantine and Yourdon methodology
b) DeMarco and Yourdon methodology
c) Gane and Sarson methodology
d) All of the mentioned
Explanation: None.
2. Which of the following is not an activity of Structured Analysis (SA) ?
a) Functional decomposition
b) Transformation of a textual problem description into a graphic model
c) All the functions represented in the DFD are mapped to a module structure
d) All of the mentioned
Explanation: The module structure is the software architecture.
3. To arrive at a form which is suitable for implementation in some programming language is the purpose of
a) Structured Analysis (SA)
b) Structured Design (SD)
c) Detailed Design (DD)
d) None of the mentioned
Explanation: None.
4. The results of structured analysis can be easily understood by ordinary customers.
a) True
b) False
Explanation: The results of structured analysis directly represents customer’s perception of the problem and uses customer’s terminology for naming different functions and data.
5. Structured Analysis is based on the principle of Bottom-Up Approach.
a) True
b) False
Explanation: Structured Analysis follows uses decomposition approach.
6. The context diagram is also known as
a) Level-0 DFD
b) Level-1 DFD
c) Level-2 DFD
d) All of the mentioned
Explanation: Context diagram captures the various entities external to the system interacting with it and data flow occurring between the system and the external entities.
7. A directed arc or line in DFD represents
a) Data Store
b) Data Process
c) Data Flow
d) All of the mentioned
Explanation: It resembles data flow in the direction of the arrow.
8. A DFD is always accompanied by a data dictionary.
a) True
b) False
Explanation: A data dictionary lists all data items appearing in a DFD including definition and data names.
9. Which of the following is a function of CASE Tool?
a) Supporting Structured analysis and design (SA/SD)
b) Maintaining the data dictionary
c) Checking whether DFDs are balanced or not
d) All of the mentioned
Explanation: None.
10. Data Store Symbol in DFD represents a
a) Physical file
b) Data Structure
c) Logical file
d) All of the mentioned
Explanation: A logical file can be a data structure or a physical file on disk.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Types of Software Metrics”.
1. Which of the following is the task of project indicators:
a) help in assessment of status of ongoing project
b) track potential risk
c) help in assessment of status of ongoing project & track potential risk
d) none of the mentioned
Explanation: None.
2. Which of the following does not affect the software quality and organizational performance?
a) Market
b) Product
c) Technology
d) People
Explanation: Market is a collection of competitors, stakeholders, users each having different views on the product. So it does not affect the software quality.
3. The intent of project metrics is:
a) minimization of development schedule
b) for strategic purposes
c) assessing project quality on ongoing basis
d) minimization of development schedule and assessing project quality on ongoing basis
Explanation: A project metric is a quantitative measure of the degree to which a system, component or process possesses an attribute.
4. Which of the following is not a direct measure of SE process?
a) Efficiency
b) Cost
c) Effort Applied
d) All of the mentioned
Explanation: Efficiency is an indirect measure.
5. Which of the following is an indirect measure of product?
a) Quality
b) Complexity
c) Reliability
d) All of the Mentioned
Explanation: All the mentioned options are indirect measures of a product.
6. In size oriented metrics, metrics are developed based on the ___________________
a) number of Functions
b) number of user inputs
c) number of lines of code
d) amount of memory usage
Explanation: None.
7. Which of the following is not an information domain required for determining function point in FPA ?
a) Number of user Input
b) Number of user Inquiries
c) Number of external Interfaces
d) Number of errors
Explanation: FPA includes five domains namely input, output, inquiries, interface and logical files.
8. Usability can be measured in terms of:
a) Intellectual skill to learn the system
b) Time required to become moderately efficient in system usage
c) Net increase in productivity
d) All of the mentioned
Explanation: None.
9. A graphical technique for finding if changes and variation in metrics data are meaningful is known as
a) DRE (Defect Removal Efficiency)
b) Function points analysis
c) Control Chart
d) All of the mentioned
Explanation: Others options are formulas.
10. Defects removal efficiency (DRE)depends on:
a) E – errors found before software delivery
b) D – defects found after delivery to user
c) Both E and D
d) Varies with project
Explanation: DRE = E / (E + d).
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Metrics Analysis”.
1. Which of the following is not a metric for design model?
a) Interface design metrics
b) Component-level metrics
c) Architectural metrics
d) Complexity metrics
Explanation: Complexity metrics measure the logical complexity of source code.
2. Statement and branch coverage metrics are part of
a) Analysis Model
b) Testing
c) Design Model
d) Source Code
Explanation: These metrics lead to the design of test cases that provide program coverage.
3. Function Points in software engineering was first proposed by
a) Booch
b) Boehm
c) Albrecht
d) Jacobson
Explanation: First proposed by Albrecht in 1979, hundreds of books and papers have been written on functions points since then.
4. How many Information Domain Values are used for Function Point Computation?
a) three
b) four
c) five
d) six
Explanation: The five values are: External Inputs, External Outputs, External Inquiries, Internal Logical Files and External Interface Files.
5. Function Point Computation is given by the formula
a) FP = [count total * 0.65] + 0.01 * sum(Fi)
b) FP = count total * [0.65 + 0.01 * sum(Fi)].
c) FP = count total * [0.65 + 0.01] * sum(Fi)
d) FP = [count total * 0.65 + 0.01] * sum(Fi)
Explanation: Option b is the correct formula for Function Point Computation.
6. Architectural Design Metrics are ___________ in nature.
a) Black Box
b) White Box
c) Gray Box
d) Green Box
Explanation: They are “black box” in that they do not require any knowledge of the inner workings of a particular software component.
7. Structural complexity of a module i is given as S(i) = f*f (i). What does f symbolizes here?
a) “fan check-out” of module i
b) “fan check-in” of module i
c) “fan in” of module i
d) “fan out” of module i
Explanation: Fan out is number of modules directly invoked by module i.
8. SMI stands for
a) Software Mature Indicator
b) Software Maturity Index
c) Software Mature Index
d) Software Maturity Indicator
Explanation: None.
9. As the SMI approaches 1.0, the software product starts becoming unstable
a) True
b) False
Explanation: As the SMI approaches 1.0, the software product begins to stabilize.
10. SMI = [Mt – (Fa + Fc + Fd)]/Mt. Here Mt is the number of modules
a) in the current release
b) in the current release that have been changed
c) from the preceding release that were deleted in the current release
d) none of the mentioned
Explanation: None.
11. The amount of time that the software is available for use is known as
a) Reliability
b) Usability
c) Efficiency
d) Functionality
Explanation: None.
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Project Management”.
1. Which of the following is not project management goal?
a) Keeping overall costs within budget
b) Delivering the software to the customer at the agreed time
c) Maintaining a happy and well-functioning development team
d) Avoiding customer complaints
Explanation: Projects need to be managed because professional software engineering is always subject to organizational budget and schedule constraints.
2. Project managers have to assess the risks that may affect a project.
a) True
b) False
Explanation: Risk management involves anticipating risks that might affect the project schedule or the quality of the software being developed, and then taking action to avoid these risks.
3. Which of the following is not considered as a risk in project management?
a) Specification delays
b) Product competition
c) Testing
d) Staff turnover
Explanation: Testing is a part of project, thus it can’t be categorized as risk.
4. The process each manager follows during the life of a project is known as
a) Project Management
b) Manager life cycle
c) Project Management Life Cycle
d) All of the mentioned
Explanation: A proven methodical life cycle is necessary to repeatedly implement and manage projects successfully.
5. A 66.6% risk is considered as
a) very low
b) low
c) moderate
d) high
Explanation: The probability of the risk might be assessed as very low (<10%), low (10–25%), moderate (25–50%), high (50–75%), or very high (>75%).
6. Which of the following is/are main parameters that you should use when computing the costs of a software development project?
a) travel and training costs
b) hardware and software costs
c) effort costs (the costs of paying software engineers and managers)
d) all of the mentioned
Explanation: Estimation involves working out how much effort is required to complete each activity and, from this, calculating the total cost of activities.
7. Quality planning is the process of developing a quality plan for
a) team
b) project
c) customers
d) project manager
Explanation: The quality plan should set out the desired software qualities and describe how these are to be assessed.
8. Which of the following is incorrect activity for the configuration management of a software system?
a) Internship management
b) Change management
c) Version management
d) System management
Explanation: Configuration management policies and processes define how to record and process proposed system changes, how to decide what system components to change, how to manage different versions of the system and its components, and how to distribute changes to customers.
9. Identify the sub-process of process improvement
a) Process introduction
b) Process analysis
c) De-processification
d) Process distribution
Explanation: The current process is assessed, and process weaknesses and bottlenecks are identified.
10. An independent relationship must exist between the attribute that can be measured and the external quality attribute.
a) True
b) False
Explanation: The value of the quality attribute must be related, in some way, to the value of the attribute than can be measured.
This set of Software Engineering Question Bank focuses on “Decomposition Techniques in Software Project Planning”.
1. Why is decomposition technique required?
a) Software project estimation is a form of problem solving
b) Developing a cost and effort estimate for a software project is too complex
c) All of the mentioned
d) None of the mentioned
Explanation: For these reasons, we decompose the problem, re-characterizing it as a set of smaller problems.
2. Cost and effort estimation of a software uses only one forms of
decomposition, either decomposition of the problem or decomposition of
the process.
a) True
b) False
Explanation: Estimation uses one or both forms of partitioning.
3. If a Direct approach to software project sizing is taken, size can be measured in
a) LOC
b) FP
c) LOC and FP
d) None of the mentioned
Explanation: LOC or Line of Code is a direct measure to estimate project size.
4. Which software project sizing approach develop estimates of the information domain characteristics?
a) Function point sizing
b) Change sizing
c) Standard component sizing
d) Fuzzy logic sizing
Explanation: None.
5. The expected value for the estimation variable (size), S, can be
computed as a weighted average of the optimistic(Sopt), most likely
(Sm), and pessimistic (Spess) estimates given as
a) EV = (Sopt + 4Sm + Spess)/4
b) EV = (Sopt + 4Sm + Spess)/6
c) EV = (Sopt + 2Sm + Spess)/6
d) EV = (Sopt + 2Sm + Spess)/4
Explanation: This assumes that there is a very small probability that the actual size result will fall outside the optimistic or pessimistic values.
6. How many forms exists of Barry Boehm’s COCOMO Model?
a) Two
b) Three
c) Four
d) No form exists
Explanation: The three forms include the basic, intermediate and advanced COCOMO model.
7. Who suggested the four different approaches to the sizing problem?
a) Putnam
b) Myers
c) Boehm
d) Putnam and Myers
Explanation: None.
8. In many cases, it is often more cost-effective to acquire, rather than develop, computer software.
a) True
b) False
Explanation: Managers are faced with a make-buy decision in such situations.
9. A make-buy decision is based on whether
a) The software may be purchased off-the-shelf
b) “Full-experience” or “Partial-experience” software components should be used
c) Customer-built software should be developed
d) All of the mentioned
Explanation: None..
10. Which of the following is not one of the five information domain characteristics of Function Point (FP) decomposition?
a) External inputs
b) External outputs
c) External process
d) External inquiries
Explanation: External inputs, external outputs, external inquiries, internal logical files, external interface files are the five domains.
11. The project planner must reconcile the estimates based on decomposition techniques to produce a single estimate of effort.
a) True
b) False
Explanation: The planner must determine the cause of divergence and then reconcile the estimates.
Explanation: None.
13. If an Indirect approach is taken, then the sizing approach is represented as
a) LOC
b) FP
c) Fuzzy Logic
d) LOC and FP
Explanation: A function point (FP) is a unit of measurement to express the amount of business functionality an information system provides to a user.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Maintenance – 1”.
1. Software Maintenance includes
a) Error corrections
b) Enhancements of capabilities
c) Deletion of obsolete capabilities
d) All of the mentioned
Explanation: None.
2. Maintenance is classified into how many categories ?
a) two
b) three
c) four
d) five
Explanation: Adaptive, corrective, perfective and preventive are the four types of software maintenance.
3. The modification of the software to match changes in the ever
changing environment, falls under which category of software
maintenance?
a) Corrective
b) Adaptive
c) Perfective
d) Preventive
Explanation: None.
4. How many phases are there in Taute Maintenance Model?
a) six
b) seven
c) eight
d) nine
Explanation: None.
5. What type of software testing is generally used in Software Maintenance?
a) Regression Testing
b) System Testing
c) Integration Testing
d) Unit Testing
Explanation: All other options are known as levels of software testing which further have types of software testing.
6. Regression testing is a very expensive activity.
a) True
b) False
Explanation: As regression testing is performed many times over the life of the software product, it becomes a costly affair.
7. Selective retest techniques may be more economical than the
“retest-all”technique.How many selective retest techniques are there?
a) two
b) three
c) four
d) five
Explanation: The three categories include: Coverage, Minimization and Safe techniques.
8. Which selective retest technique selects every test case that
causes a modified program to produce a different output than its
original version?
a) Coverage
b) Minimization
c) Safe
d) Maximization
Explanation: Safe techniques do not focus on coverage criteria, instead they select every test case that cause a modified program to produce different output than its original version.
9. ______________ measures the ability of a regression test selection technique to handle realistic applications.
a) Efficiency
b) Precision
c) Generality
d) Inclusiveness
Explanation: Generality measures the ability of a technique to handle realistic and diverse language constructs, arbitrarily complex modifications, and realistic testing applications.
10. Which regression test selection technique exposes faults caused by modifications?
a) Efficiency
b) Precision
c) Generality
d) Inclusiveness
Explanation: Inclusiveness measures the extent to which a technique chooses test cases that will cause the modified program to produce different output than the original program, and thereby expose faults caused by modifications.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Process Improvement”.
1. “Robustness” answers which of the following description?
a) CASE tools be used to support the process activities
b) Process errors are avoided or trapped before they result in product errors
c) Defined process is acceptable and usable by the engineers responsible for producing the software
d) Process continues in spite of unexpected problems
Explanation: None.
2. Process improvement is the set of activities, methods, and
transformations that developers use to develop and maintain information
systems.
a) True
b) False
Explanation: The definition is of a system development process.
3. “Understandability” answers which of the following description?
a) The extent to which the process is explicitly defined
b) Process errors are avoided or trapped before they result in product errors
c) Defined process is acceptable and usable by the engineers responsible for producing the software product
d) Process continues in spite of unexpected problems
Explanation: None.
4. How many stages are there in process improvement?
a) three
b) four
c) five
d) six
Explanation: Process measurement, analysis and change are the three stages.
5. In which stage of process improvement bottlenecks and weaknesses are identified?
a) Process measurement
b) Process analysis
c) Process change
d) None of the mentioned
Explanation: In Process analysis the current process is assessed and bottlenecks and weaknesses are identified.
6. Prototypes and 4GL business systems are categorized under which process?
a) Informal
b) Managed
c) Methodical
d) Supported
Explanation: Here the development team chose their own way of working.
7. The documentation of a process which records the tasks, the roles and the entities used is called
a) Process metric
b) Process analysis
c) Process modelling
d) None of the mentioned
Explanation: Process models may be presented from different perspectives.
8. It is always best to start process analysis with a new test model.
a) True
b) False
Explanation: It is always best to start process analysis with an existing model. People then may extend and change this.
9. What is a tangible output of an activity that is predicted in a project plan?
a) Deliverable
b) Activity
c) Condition
d) Process
Explanation: None.
10. What is often undefined and is left to the ingenuity of the project managers and engineers?
a) Role
b) Exception
c) Activity
d) Process
Explanation: Exceptions are often undefined and it is left to the ingenuity of the project managers and engineers to handle the exception.
11. Which of the following is not a part of process change?
a) Introducing new practices, methods or processes
b) Introducing new team members to existing project
c) Introducing or removing deliverable
d) Introducing new roles or responsibilities
Explanation: Adding more developers aid to process completion rather than changing it.
Explanation: The CMM is discrete rather than continuous.
13. The CMMI assessment is based on a x-point scale. What is the value of x?
a) 0
b) 2
c) 4
d) 6
Explanation: Not performed, performed, managed, defined, quantitatively managed, and optimizing are the six points.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Architectural Design”.
1. Architectural design is a creative process satisfying only functional-requirements of a system.
a) True
b) False
Explanation: In architectural design you design a system organization satisfying the functional and non-functional requirements of a system.
2. A ________ view shows the system hardware and how software components are distributed across the processors in the system.
a) physical
b) logical
c) process
d) all of the mentioned
Explanation: A physical view is implemented by system engineers implementing the system hardware.
3. The UML was designed for describing _________
a) object-oriented systems
b) architectural design
c) SRS
d) Both object-oriented systems and Architectural design
Explanation: The UML was designed for describing object-oriented systems and, at the architectural design stage, you often want to describe systems at a higher level of abstraction.
4. Which of the following view shows that the system is composed of interacting processes at run time?
a) physical
b) development
c) logical
d) process
Explanation: This view is useful for making judgments about non-functional system characteristics such as performance and availability.
5. Which of the following is an architectural conflict?
a) Using large-grain components improves performance but reduces maintainability
b) Introducing redundant data improves availability but makes security more difficult
c) Localizing safety-related features usually means more communication so degraded performance
d) All of the mentioned
Explanation: High availability architecture can be affected by several design factors that are required to be maintained to ensure that no single points of failure exist in such design.
6. Which of the following is not included in Architectural design decisions?
a) type of application
b) distribution of the system
c) architectural styles
d) testing the system
Explanation: Architectural design decisions include decisions on the type of application, the distribution of the system, the architectural styles to be used, and the ways in which the architecture should be documented and evaluated.
7. Architecture once established can be applied to other products as well.
a) True
b) False
Explanation: Systems in the same domain often have similar architectures that reflect domain concepts.
8. Which of the following pattern is the basis of interaction management in many web-based systems?
a) architecture
b) repository pattern
c) model-view-controller
d) different operating system
Explanation: Model-View-Controller pattern is the basis of interaction management in many web-based systems.
9. What describes how a set of interacting components can share data?
a) model-view-controller
b) architecture pattern
c) repository pattern
d) none of the mentioned
Explanation: The majority of systems that use large amounts of data are organized around a shared database or repository.
10. Which view in architectural design shows the key abstractions in the system as objects or object classes?
a) physical
b) development
c) logical
d) process
Explanation: It is possible to relate the system requirements to entities in a logical view.
Explanation: All these models reflects the basic strategy that is used to structure a system.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Application Architectures”.
1. Which of the following examples is/are models of application architectures?
a) a means of assessing components for reuse
b) a design checklist
c) a vocabulary for talking about types of applications
d) all of the mentioned
Explanation: Application architectures encapsulate the principal characteristics of a class of systems.
2. ERP stands for
a) Enterprise Research Planning
b) Enterprise Resource Planning
c) Enterprise Resource Package
d) Enterprise Research Package
Explanation: None.
3. Which of the following type describes application architectures?
a) Transaction processing applications
b) Language processing systems
c) Client management systems
d) Transaction processing applications and Language processing systems
Explanation: Transaction processing applications are database-centered applications that process user requests for information and update the information in a database, while language processing systems are systems in which the user’s intentions are expressed in a formal language.
4. All the operations in a transaction need to be completed before the database changes are made ________
a) functional
b) available to the users
c) permanent
d) none of the mentioned
Explanation: This ensures that failure of operations within the transaction does not lead to inconsistencies in the database.
5. Systems that involve interaction with a shared database can be considered as.
a) software-based
b) transaction-based
c) server-based
d) client-based
Explanation: Such systems with a shared database are also referred to as transaction based information systems.
6. What translates a natural or an artificial language into another
representation of that language and, for programming languages also
execute the resulting code?
a) ERP systems
b) Transaction-based information systems
c) Language processing systems
d) None of the mentioned
Explanation: In software engineering, compilers translate an artificial programming language into machine code.
7. Properties of a system such as performance and security are independent of the architecture used.
a) True
b) False
Explanation: Properties such as performance, security, and availability are influenced by the architecture used.
8. Which of the following is/are commonly used architectural pattern(s)?
a) Model-View-Controller
b) Layered Architecture
c) Client–server
d) All of the mentioned
Explanation: Commonly used architectural patterns include Model-View-Controller, Layered Architecture, Repository, Client–server, and Pipe and Filter.
9. A language-processing systems may translate an XML data description into
a) a machine code
b) an alternative XML representation
c) machine code and alternative XML representation
d) a software module
Explanation: Such is the property and function of language processing system.
10. Transaction processing systems may be organized as a _________
architecture with system components responsible for input, processing,
and output.
a) Repository
b) Client–server
c) Model-View-Controller
d) Pipe and Filter
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Unified Modelling Language”.
1. Object oriented analysis and design can be handled by the one who knows UML.
a) True
b) False
Explanation: The Unified Modeling Language includes a set of graphic notation techniques to create visual models of object-oriented software-intensive systems.
2. At Conceptual level Class diagrams should include
a) operations only
b) attributes only
c) both operations and attributes
d) none of the mentioned
Explanation: In software engineering, a class diagram in the Unified Modeling Language (UML) is a type of static structure diagram that describes the structure of a system by showing the system’s classes, their attributes, operations, and the relationships among objects.
3. Select the statement true for activity diagrams.
a) They can be used to discover parallel activities
b) They are used to depict workflow for a particular business activity
c) Activity diagram do not tell who does what and are difficult to trace back to object models
d) All of the mentioned
Explanation: Activity diagrams are graphical representations of workflows of step wise activities and actions with support for choice, iteration and concurrency.
4. Constraints can be represented in UML by
a) {text}
b) [text].
c) Constraint
d) None of the mentioned
Explanation: Constraints are represented by {text string}.
5. What is an object?
a) An object is an instance of a class
b) An object includes encapsulation of data
c) An object is not an instance of a class
d) All of the mentioned
Explanation: An object is an instance of a class.
6. What is an abstract class?
a) A class that has direct instances, but whose descendants may have direct instances
b) A class that has direct instances, but whose descendants may not have direct instances
c) A class that has no direct instances, but whose descendants may have direct instances
d) All of the mentioned
Explanation: An abstract type is a type in a nominative type system which cannot be instantiated directly.
7. Which of the following are the valid relationships in Use Case Diagrams
a) Generalization
b) Include
c) Extend
d) All of the mentioned
Explanation: Generalization, include, extend all of these are valid relationships in use case diagrams.
8. Which of the following statement(s) is true about interaction diagrams?
a) Interaction diagrams are at their best when they deal with one main design flow and not multiple variants that can happen
b) Interaction diagrams are good at designing part or all of one use case’s functionality across multiple objects
c) Interaction diagrams allow the analyst to show iteration and conditional execution for messaging between objects
d) All of the mentioned
Explanation: Interaction diagram is used to describe some type of interactions among the different elements in the model. So this interaction is a part of dynamic behaviour of the system.
9. UML interfaces are used to:
a) specify required services for types of objects
b) program in Java, but not in C++ or Smalltalk
c) define executable logic to reuse across classes
d) define an API for all classes
Explanation: An interface is like a template design for a class that contains no data or implementation; only definitions for methods, properties etc.
10. Referring to the attached diagram, the arrow indicates:
a) Navigability
b) Dependency
c) Association
d) Refers to
Explanation: The arrows describe the ways you can navigate.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Analysis Modelling”.
1. Which of the following is not the primary objectives in the analysis model?
a) describing the customer complaints
b) establishing a basis for the creation of a software design
c) defining a set of requirements that can be validated once the software is built
d) none of the mentioned
Explanation: All the options are covered in analysis model.
2. A description of each function presented in the DFD is contained in a ________
a) data flow
b) process specification
c) control specification
d) data store
Explanation: None.
3. Which diagram indicates the behaviour of the system as a consequence of external events?
a) data flow diagram
b) state transition diagram
c) control specification diagram
d) workflow diagram
Explanation: The state transition diagram represents the various modes of behavior (called states) of the system and the manner in which transitions are made from state to state.
4. A data model contains
a) data object
b) attributes
c) relationships
d) all of the mentioned
Explanation: The data model consists of three interrelated pieces of information: the data object,
the attributes that describe the data object, and the relationships that connect data objects to one another.
5. _________ defines the properties of a data object and take on one of the three different characteristics.
a) data object
b) attributes
c) relationships
d) data object and attributes
Explanation: They can be used to name an instance of the data object, describe the instance, or make reference to another instance in another table.
6. The __________ of a relationship is 0 if there is no explicit need
for the relationship to occur or the relationship is optional.
a) modality
b) cardinality
c) entity
d) structured analysis
Explanation: The modality is 1 if an occurrence of the relationship is mandatory, else 0 for optional relationship.
7. A _________ is a graphical representation that depicts information
flow and the transforms that are applied as data moves from input to
output.
a) data flow diagram
b) state transition diagram
c) control specification
d) workflow diagram
Explanation: The basic form of a data flow diagram, also known as a data flow graph or a bubble chart.
8. A data condition occurs whenever a data is passed to an input
element followed by a processing element and the result in control
output.
a) True
b) False
Explanation: Standard flow of condition check.
9. The __________ enables the software engineer to develop models of
the information domain and functional domain at the same time
a) data flow diagram
b) state transition diagram
c) control specification
d) activity diagram
Explanation: As the DFD is refined into greater levels of detail, the analyst performs an implicit functional decomposition of the system, thereby accomplishing the fourth operational analysis principle for function.
10. The __________ contains a state transition diagram that is a sequential specification of behavior.
a) data flow diagram
b) state transition diagram
c) control specification
d) workflow diagram
Explanation: The control specification(CSPEC) describes the behavior of the system, but it gives us no information about the inner working of the processes that are activated as a result of this behavior .
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Reuse”.
1. Reuse-based software engineering is a software engineering
strategy where the development process is geared to reusing existing
software.
a) True
b) False
Explanation: None.
2. The open source movement has meant that there is a huge reusable code base available at
a) free of cost
b) low cost
c) high cost
d) short period of time
Explanation: The open source movement has meant that there is a huge reusable code base available at low cost. This may be in the form of program libraries or entire applications.
3. Consider the example and categorize it accordingly, “A
pattern-matching system developed as part of a text-processing system
may be reused in a database management system”.
a) Application system reuse
b) Component reuse
c) Object and function reuse
d) None of the mentioned
Explanation: Components of an application, ranging in size from subsystems to single objects, may be reused.
4. COTS stands for
a) Commercial Off-The-Shelf systems
b) Commercial Off-The-Shelf states
c) Commercial Off-The-System state
d) None of the mentioned
Explanation: None.
5. COTS product reuse means
a) Class and function libraries that implement commonly used abstractions are available for reuse
b) Shared components are woven into an application at different places when the program is compiled
c) Large-scale systems that encapsulate generic business functionality and rules are configured for an organization
d) Systems are developed by configuring and integrating existing application systems
Explanation: None.
6. .NET are specific to which platform?
a) Java
b) Mac-OS
c) Microsoft
d) LINUX
Explanation: NET Framework (pronounced dot net) is a software framework developed by Microsoft that runs primarily on Microsoft Windows.
7. Which of the following is a generic structure that is extended to create a more specific subsystem or application?
a) Software reuse
b) Object-oriented programming language
c) Framework
d) None of the mentioned
Explanation: Frameworks are implemented as a collection of concrete and abstract object classes in an object-oriented programming language.
8. “An ordering system may be adapted to cope with a centralized
ordering process in one company and a distributed process in another.”
Which category the example belong to?
a) Process specialization
b) Platform specialization
c) Environment specialization
d) Functional specialization
Explanation: In process specialization, the system is adapted to cope with specific business processes.
9. What are generic application systems that may be designed to
support a particular business type, activity, or sometimes a complete
enterprise?
a) COTS-solution systems
b) COTS-integrated systems
c) ERP systems
d) Both COTS-solution and COTS-integrated systems
Explanation: None
10. Which of the following is not an advantages of software reuse?
a) lower costs
b) faster software development
c) high effectiveness
d) lower risks
Explanation: Effectiveness depends on how one reuses the existing product.
11. ERP stands for
a) Effective Reuse Planning
b) Enterprise Resource Planning
c) Effective Research Planning
d) None of the mentioned
Explanation: Enterprise Resource Planning systems are examples of large-scale COTS reuse.
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Distributed Software Engineering”.
1. Which of the following term is best defined by the statement “In a
distributed system, several processes may operate at the same time on
separate computers on the network.”?
a) Concurrency
b) Openness
c) Resource sharing
d) Fault tolerance
Explanation: None.
2. Which of the following is not a dimension of scalability?
a) Size
b) Distribution
c) Manageability
d) Interception
Explanation: Interception is a communication conception.
3. A distributed system must defend itself against
a) Modification
b) Interruption
c) Fabrication
d) All of the mentioned
Explanation: None.
4. QoS stands for
a) Quality of security
b) Quality of system
c) Quality of service
d) None of the mentioned
Explanation: QoS is particularly critical when the system is dealing with time-critical data such as sound or video streams.
5. In Java,_________ are comparable with, though not identical to, RPCs.
a) Remote Method Invocations
b) Operating System
c) Client–server computing
d) None of the mentioned
Explanation: The RMI framework handles the invocation of remote methods in a Java program.
6. _________ depend on there being a clear separation between the
presentation of information and the computations that create and process
that information.
a) Master-slave architectures
b) Client–server systems
c) Two-tier client–server architecture
d) Both Master-slave architectures AND Client–server systems
Explanation: One should design the architecture of distributed client–server systems so that they are structured into several logical layers, with clear interfaces between these layers.
7. Which architecture is used when there is a high volume of transactions to be processed by the server?
a) Multi-tier client–server architecture
b) Master-slave architecture
c) Distributed component architecture
d) Peer-to-peer architecture
Explanation: Multi-tier systems may be used when applications need to access and use data from different databases.
8. Which architecture are reliant on middle-ware?
a) Multi-tier client–server architecture
b) Master-slave architecture
c) Distributed component architecture
d) Peer-to-peer architecture
Explanation: It allows the system designer to delay decisions on where and how services should be provided.
9. __________ is a way of providing functionality on a remote server with client access through a web browser.
a) SaaS
b) SOA
c) Configurability
d) Both SaaS and Configurability
Explanation: The server maintains the user’s data and state during an interaction session.
10. Which architecture decentralized architectures in which there are no distinguished clients and servers?
a) Multi-tier client–server architecture
b) Master-slave architecture
c) Distributed component architecture
d) Peer-to-peer architecture
Explanation: Peer-to-peer (p2p) systems are decentralized systems in which computations may be carried out by any node on the network.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Web Engineering”.
1. Which web app attribute is defined by the statement:”A large number of users may access the WebApp at one time”?
a) Unpredictable load
b) Performance
c) Concurrency
d) Network intensiveness
Explanation: None.
2. Which web app attribute is defined by the statement:”The quality
and aesthetic nature of content remains an important determinant of the
quality of a WebApp”?
a) Availability
b) Data driven
c) Content sensitive
d) Continuous evolution
Explanation: None.
3. If the user queries a collection of large databases and extracts information from the webapp, the webapp is categorized under
a) Service oriented app
b) Database access app
c) Portal app
d) Data warehousing app
Explanation: The Data Warehouse is a stable, read-only database that combines information from separate systems into one, easy-to-access location.
4. Which process model should be used in virtually all situations of web engineering?
a) Incremental Model
b) Waterfall Model
c) Spiral Model
d) None of the mentioned
Explanation: The web engineering process must accommodate incremental delivery, frequent changes and short timeline.
5. Which analysis is a part of Analysis model of the web engineering process framework?
a) Content Analysis
b) Interaction Analysis
c) Functional Analysis
d) All of the mentioned
Explanation: Analysis model establishes a basis for design which requires all the mentioned options.
6. Web development and software development are one and the same thing.
a) True
b) False
Explanation: They are different due to the nature and distinct requirements of Web-based systems.
7. Web-based systems are often document-oriented containing static or dynamic content.
a) True
b) False
Explanation: In web-based systems, more emphasis is on “look and feel” of the product.
8. Web-based systems apply the same levels of formal planning and testing used in software development.
a) True
b) False
Explanation: Web-based systems are typically constrained to a short development time making it difficult to apply the same levels of formal planning and testing used in software development.
9. Which of the following statements are incorrect with reference to web-based systems? Web-based systems
a) should be unscalable
b) must be able to cope with uncertain, random heavy demands on services
c) must be secure
d) are subject to assorted legal, social, and ethical scrutiny
Explanation: Web-based systems should be scalable.
10. What category of web-based system would you assign to electronic shopping?
a) Informational
b) Interactive
c) Transaction-oriented
d) Workflow-oriented
Explanation: It involves usage of transaction management of database systems.
11. What category of web-based system would you assign to discussion groups?
a) Collaborative work
b) Online communities
c) Web portals
d) Workflow-oriented
Explanation: None.
Explanation: W3C is an international consortium where member organizations, a full-time staff, and the public work together to develop web standards.
13. Which of the following is a risk associated with using hypertext in web applications?
a) Loss of sense of locality and direction
b) Cognitive overload for users
c) All of the mentioned
d) None of the mentioned
Explanation: Hypertexts and links may divert the users attention from the main content.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Computer Aided Software Engineering”.
1. Which of the following is software engineer’s primary characteristics?
a) A collection of useful tools that will help in every step of building a product
b) An organized layout that enables tools to be found quickly and used efficiently
c) A skilled artisan who understands how to use the tools in an effective manner
d) All of the mentioned
Explanation: None.
2. Database management software serves as a foundation for the establishment of a CASE database (repository) that we call
a) project database
b) system database
c) analysis and design tools
d) prototyping tools
Explanation: Given the emphasis on configuration objects, database management tools for CASE are evolving from relational database management systems to object oriented database management systems.
3. What enables a software engineer to defined screen layout rapidly for interactive applications?
a) Analysis and design tools
b) Tool kit
c) Screen painters
d) PRO/SIM tools
Explanation: More sophisticated CASE prototyping tools enable the creation of a data design, coupled with both screen and report layouts.
4. _________tools assist in the planning, development, and control in CASE.
a) Dynamic measurement
b) Data acquisition
c) Test management
d) Cross-functional tools
Explanation: None.
5. Which tools cross the bounds of the preceding categories?
a) Data acquisition
b) Dynamic measurement
c) Cross-functional tools
d) Simulation
Explanation: None.
6. Which environment demands specialized testing tools that exercise
the graphical user interface and the network communications requirements
for client and server?
a) Dynamic analysis
b) Client/Server
c) Re-engineering
d) Test management
Explanation: A client/server architecture is GUI based.
7. Which tools are used to modify online database systems?
a) Reverse engineering specification tools
b) Code restructuring and analysis tools
c) Test management tools
d) online system re-engineering tools
Explanation: For example these tools convert IDMS or DB2 files into entity-relationship format.
8. Which is the definition of objects in the database that leads
directly to a standard approach for the creation of software engineering
documents.
a) Document standardization
b) Data integrity
c) Information sharing
d) Data/data integration
Explanation: None.
9. Which of the following term is best defined by the statement:
“CASE tools and the target applications are isolated from physical
storage so they are not affected when the hardware configuration is
changed.”?
a) Non-redundant data storage
b) Data independence
c) Data dependence
d) Ad Hhoc data queries and reports
Explanation: None.
10. Which of the following term is best define by the statement:”Each
object is stored only once, but is accessible by all CASE tools that
need it.”?
a) Non-redundant data storage
b) Data independence
c) Transaction control
d) Ad Hoc data queries and reports
Explanation: None.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Reliability”.
1. Which of the following is not a phase of “bathtub curve” of hardware reliability?
a) Useful Life
b) Burn-in
c) Wear-out
d) Time
Explanation: Time is the horizontal dimension on which the bathtub curve is built and not the phase.
2. How is reliability and failure intensity related to each other?
a) direct relation
b) inverse relation
c) no relation
d) none of the mentioned
Explanation: As the reliability increases, failure intensity decreases.
3. How many product quality factors are proposed in McCall quality model?
a) 2
b) 3
c) 11
d) 8
Explanation: McCall quality model has three product quality factors namely: Product revision, Product operation, Product Transition .
4. Which one of the following is not a software quality model?
a) ISO 9000
b) McCall model
c) Boehm model
d) ISO 9126
Explanation: ISO-9000 series of standards is a set of document dealing with quality systems that can be used for quality assurance purposes.
5. What is MTTF ?
a) Maximum time to failure
b) Mean time to failure
c) Minimum time to failure
d) None of the mentioned
Explanation: None.
6. How is software reliability defined?
a) time
b) efficiency
c) quality
d) speed
Explanation: Software Reliability mainly concerned with the time component. It can be seen in various models like Basic Execution Time Model and Logarithmic Poisson Execution Time Model.
7. Suitability, Accuracy, Interoperability, and security are what type quality attribute of ISO 9126 ?
a) Reliability
b) Efficiency
c) Functionality
d) Usability
Explanation: All the Characteristics mentioned in the question are related to achievement of the basic purpose for which the software is being engineered, which is functionality.
8. Time Behavior and Resource Behavior fall under which quality attribute of ISO 9126 ?
a) Reliability
b) Efficiency
c) Functionality
d) Usability
Explanation: The Characteristics mentioned in the question are related to the relationship between the level of performance of the software and the amount of resources used, under stated conditions.
9. NHPP stands for
a) Non Homogeneous Poisson Product
b) Non-Hetrogeneous Poisson Product
c) Non-Hetrogeneous Poisson Process
d) Non Homogeneous Poisson Process
Explanation: None.
10. The CMM model is a technique to
a) automatically maintain the software reliability
b) improve the software process.
c) test the software
d) all of the mentioned
Explanation: Capability Maturity Model (CMM) is a strategy for improving the software process, irrespective of the actual life cycle model used.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Reliability Models”.
1. Which one is not a software quality model?
a) ISO 9000
b) McCall model
c) Boehm model
d) ISO 9126
Explanation: ISO 9000 is software certification.
2. How many levels are present in CMM?
a) three
b) four
c) five
d) six
Explanation: The five levels are: initial, repeatable, defined, managed, optimizing.
3. Which level of CMM is for process management?
a) Initial
b) Repeatable
c) Defined
d) Optimizing
Explanation: It is a characteristic of processes at this level that the focus is on continually improving process performance through both incremental and innovative technological changes/improvements.
4. In ISO 9126, time behavior and resource utilization are a part of
a) maintainability
b) portability
c) efficiency
d) usability
Explanation: A set of attributes that bear on the relationship between the level of performance of the software and the amount of resources used, under stated conditions.
5. Which of the following is not a Probabilistic Model?
a) Error seeding
b) NHPP
c) Input domain
d) Halstead’s software metric
Explanation: Halstead’s software metric is a deterministic model.
6. Software reliability is defined with respect to
a) time
b) bugs
c) failures
d) quality
Explanation: None.
7. Failure In Time (FIT) is another way of reporting
a) MTTR
b) MTTF
c) MTSF
d) MTBF
Explanation: FIT reports the number of expected failures per one billion hours of operation for a device. This term is used particularly by the semiconductor industry but is also used by component manufacturers .
8. MTTF stands for
a) Minimum time to failure
b) Mean time to failure
c) Maximum time to failure
d) None of the mentioned
Explanation: None.
9. Mean Time To Repair (MTTR) is the time needed to repair a failed hardware module.
a) True
b) False
Explanation: In an operational system, repair generally means replacing a failed hardware part. Thus, hardware MTTR could be viewed as mean time to replace a failed hardware module.
10. IMC Networks is a leading ________ certified manufacturer of
optical networking and LAN/WAN connectivity solutions for enterprise,
telecommunications and service provider applications.
a) Telco Systems
b) D-Link
c) Arista Networks
d) ISO 9001
Explanation: Founded in 1988, with over one million products installed worldwide, IMC Networks offers a wide range of fiber media and mode converters for a variety of applications.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Software Testing Techniques – 1”.
1. Which of the following term describes testing?
a) Finding broken code
b) Evaluating deliverable to find errors
c) A stage of all projects
d) None of the mentioned
Explanation: Software testing is the process of evaluation a software item to detect differences between given input and expected output.
2. What is Cyclomatic complexity?
a) Black box testing
b) White box testing
c) Yellow box testing
d) Green box testing
Explanation: Cyclomatic complexity measures the amount of decision logic in the program module.Cyclomatic complexity gives the minimum number of paths that can generate all possible paths through the module.
3. Lower and upper limits are present in which chart?
a) Run chart
b) Bar chart
c) Control chart
d) None of the mentioned
Explanation: A run chart is used to monitor the behavior of a variable over time for a process or system. Run charts graphically display cycles, trends, shifts, or non-random patterns in behavior over time. It contains lower and upper limits.
4. Maintenance testing is performed using which methodology?
a) Retesting
b) Sanity testing
c) Breadth test and depth test
d) Confirmation testing
Explanation: Maintenance Testing is done on the already deployed software. The deployed software needs to be enhanced, changed or migrated to other hardware. The Testing done during this enhancement, change and migration cycle is known as maintenance testing.
5. White Box techniques are also classified as
a) Design based testing
b) Structural testing
c) Error guessing technique
d) None of the mentioned
Explanation: The structural testing is the testing of the structure of the system or component. Structural testing is often referred to as ‘white box’ or ‘glass box’ or ‘clear-box testing’ because in structural testing we are interested in what is happening ‘inside the system/application’.
6. Exhaustive testing is
a) always possible
b) practically possible
c) impractical but possible
d) impractical and impossible
Explanation: Exhaustive testing is the testing where we execute single test case for multiple test data.It means if we are using single test case for different product or module under manual testing.
testing .
7. Which of the following is/are White box technique?
a) Statement Testing
b) Decision Testing
c) Condition Coverage
d) All of the mentioned
Explanation: Statement testing, decision testing, condition coverage all of them uses white box technique.
8. What are the various Testing Levels?
a) Unit Testing
b) System Testing
c) Integration Testing
d) All of the mentioned
Explanation: Unit, system, integration testing all of them are levels in testing.
9. Boundary value analysis belong to?
a) White Box Testing
b) Black Box Testing
c) White Box & Black Box Testing
d) None of the mentioned
Explanation: Boundary value analysis is based on testing at the boundaries between partitions and checks the output with expected output.
10. Alpha testing is done at
a) Developer’s end
b) User’s end
c) Developer’s & User’s end
d) None of the mentioned
Explanation: Alpha testing takes place at the developer’s end. Developers observe the users and note problems. Alpha testing is testing of an application when development is about to complete. Minor design changes can still be made as a result of alpha testing.
This set of Software Engineering Multiple Choice Questions & Answers (MCQs) focuses on “Testing Tools”.
1. Standard Enforcer is a
a) Static Testing Tool
b) Dynamic Testing
c) Static & Dynamic Testing
d) None of the mentioned
Explanation: Static Testing tools are those that perform analysis of the the program without executing them at all.
2. Many applications using static analysis find 0.1-0.2% NCSS. NCSS stands for
a) Non-Code Source Statement
b) Non Comment Source Sentence
c) Non-Comment Source Statement
d) All of the mentioned
Explanation: None.
3. Which testing tool does a simple job of enforcing standards in a uniform way of many programs?
a) Static Analyzer
b) Code Inspector
c) Standard Enforcer
d) Both Code Inspector & Standard Enforcer
Explanation: A standard enforcer is just like a code inspector, except that the rules are generally simpler. Standard enforcer looks at only single statements while the static analyzer looks at whole programs.
4. Software Testing with real data in real environment is known as
a) alpha testing
b) beta testing
c) regression testing
d) none of the mentioned
Explanation: Beta testing is the last stage of testing, and normally can involve sending the product to beta test sites outside the company for real-world exposure or offering the product for a free trial download over the Internet.
5. Which of the following testing tools examine program systematically & automatically ?
a) Code Inspector
b) Static Analyzer
c) Standard Enforcer
d) Coverage Analyzer
Explanation: A static analyzer operates from a pre-computed database o descriptive information derived from the source text of the program.
6. Which testing tool is responsible for documenting programs ?
a) Test/File Generator
b) Test Harness System
c) Test Archiving Systems
d) Coverage Analyzer
Explanation: The answer is self-explanatory.
7. Beta Testing is done by
a) Developers
b) Testers
c) Users
d) All of the mentioned
Explanation: None.
8. Standard enforcer tool looks at the whole program.
a) True
b) False
Explanation: This tool looks at only single statements.
9. Debugging Program is a program which runs concurrently with the program under test & provide commands to
a) examine memory & registers
b) stop execution at a particular point
c) search for references for particular variables, constant and registers
d) all of the mentioned
Explanation: Debugging is a methodical process of finding and reducing the number of bugs, or defects, in a computer program or a piece of electronic hardware, thus making it behave as expected.
10. Execution Verifier is a dynamic tool that is also known as
a) Test File Generator
b) Coverage Analyzer
c) Output Comparator
d) Test Harness System
Explanation: None.

